AMD EPYC Processor Powered Google Cloud Confidential VMs Show Excellent Performance with Enhanced Security for Data in-Use
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Google® Cloud set a new standard for security and privacy in the cloud with their recent announcement about Confidential Virtual Machines. Google Cloud Confidential VMs use the AMD EPYC™ processor’s Secure Encrypted Virtualization to strengthen VM isolation and data-in-use protection. No changes to the application are required to take advantage of these features.
Secure Encrypted Virtualization is a hardware-based security feature of all AMD EPYC 7002-series processors enabled on select servers and cloud instances. SEV encrypts the data-in-use on a virtual machine, helping to keep it isolated from other guests, the hypervisor and even the system administrators. The SEV feature works by providing each virtual machine with an encryption key that isolates guests and the hypervisor from one another. These keys are created, distributed, and managed by the AMD Secure Processor. Memory encryption keys never leave the processor. With SEV-enabled Confidential VMs, customers have better control of their data, enabling them to better secure their workloads and collaborate in the cloud with confidence.
Confidential VMs are now available on Google Compute Engine. You can read the general availability announcement here. Confidential VMs make use of Google Compute Engine’s N2D instances and are available in both fixed and custom sizes. Similar to N2D instances, the Google Cloud Confidential VMs range from 2 vCPUs to 224 vCPUs and offer up to 896 GiB of memory. There are three different types of Google Cloud Confidential VMs: standard, highmem and highcpu, with vCPU:Memory ratios of 1:4, 1:8 & 1:2 respectively. The Google Cloud Confidential VMs also come with the support of persistent disks and local attached SSDs. With 70% greater platform memory bandwidth than comparable N1 instances, N2D instances provide over a 100% performance improvement on a variety of representative benchmarks. In addition to security features, the Google Cloud Confidential VMs also deliver similar exceptional performance on a variety of workloads to comparable standard Google VMs.
The AMD Cloud Solutions engineering team has worked closely with the Google Cloud security engineering teams to showcase the performance of Confidential VMs and demonstrate how organizations can take advantage of this transformative technology while enhancing their security landscape. Here are a few sample workload performance characterizations.
Relational Databases
Relational Database Management Systems remain the core of enterprise applications for transaction processing, business analytics and decision support systems. Moving databases to the cloud provides a host of benefits: scalability, location independence, reliability, and low administrative costs. However, performance and data security are important factors to consider before selecting a platform for deployment. Google Confidential VMs provide a solution where customers can secure their data while still enjoying great performance.
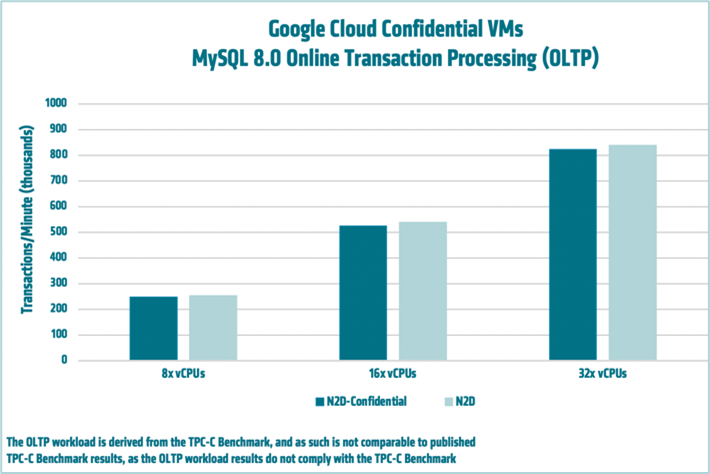
MySQL™ is a widely used open-source RDBMS based on the Structured Query Language (SQL). AMD engineers ran a benchmark comparing the performance of standard N2D VMs to Confidential N2D VMs in an online transaction processing (OLTP) deployment scenario. The figure below, showing results on 8, 16, and 32 vCPU instances, demonstrates that on average, there is a performance impact of ~2.31% when using the Confidential VMs. For more information, see MySQL on Google Compute Engine with N2D Confidential VMs.*
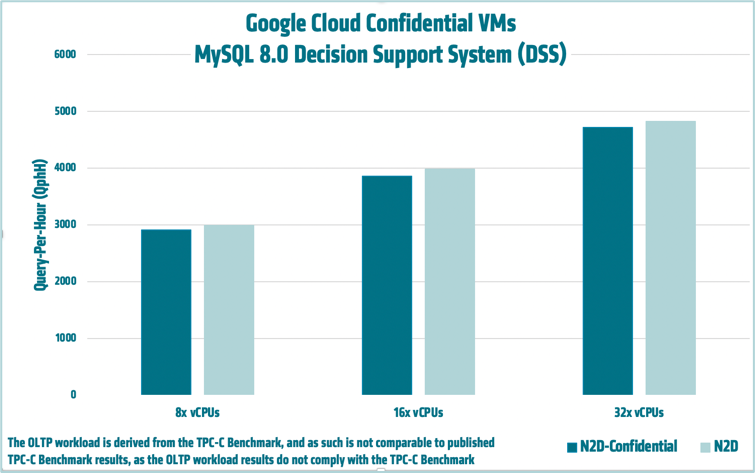
AMD engineers also ran a benchmark comparing the performance of standard N2D VMs to Confidential N2D VMs for decision support system (DSS) deployments. The figure below, showing results on 8, 16, and 32 vCPU instances, demonstrates that on average, there is a performance impact of ~2.62% when using Confidential VMs. For more information on MySQL and other databases on Google Compute Engine here.
Web Servers
Cloud-based web server hosting has increased in popularity due to its cost-effective nature, ease of setup, scalability, and resource distribution. Once again, performance and data security are important factors to consider before selecting a platform for deployment. Google Cloud Confidential VMs can provide a solution where customers can enjoy great performance while securing their data.
The Apache® HTTP Server is a popular open-source code implementation of a web server. Apache HTTP Server on Google Compute Engine supports the deployment and management of web servers with a variety of instance sizes. This flexibility provides the ability to handle fluctuating workloads in a predictable manner.
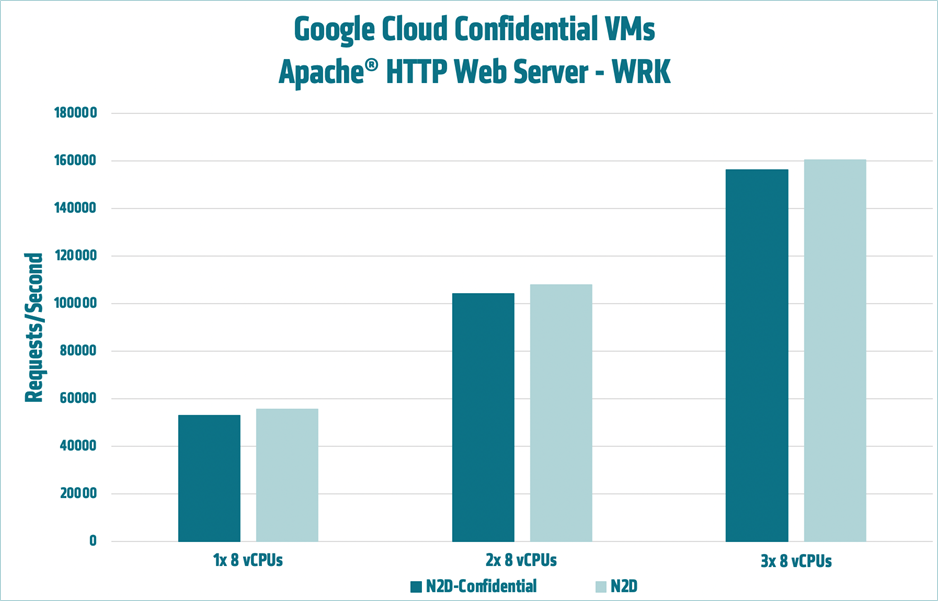
AMD engineers ran the WRK benchmark using Apache HTTP Server in order to compare the performance of standard N2D VMs to Confidential N2D VMs. The figure below, showing scale-out results on one, two and three nodes with 8 vCPU instances, demonstrates that on average, there is a performance impact of ~3.64% when using Confidential VMs. For more information, see Apache Web Server on Google Compute Engine with N2D Confidential VMs. For related information on NGINX®, see NGINX on Google Compute Engine with N2D Confidential VMs.
Graph Databases
Graph databases have a growing range of important uses including applications like fraud detection, asset management, cybersecurity and social networking. Migrating a graph database to the cloud brings numerous advantages in terms of cost and scalability but data security remains a concern.
Based on parallel graph technology, TigerGraph™ uses the power of interconnected data to offer organizations deep insights and high-impact business outcomes. TigerGraph fulfills the promise and benefits of graph analytics by tackling these data challenges in real time.
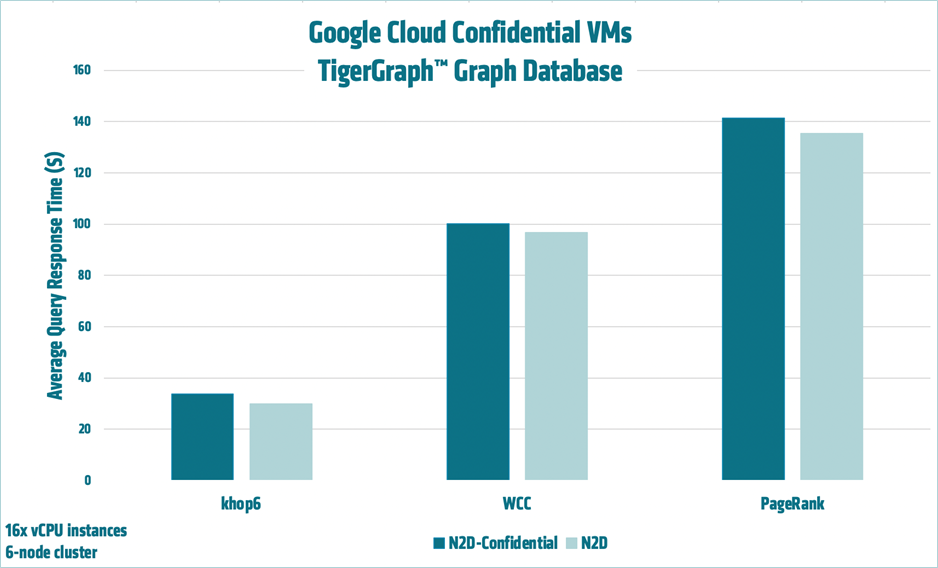
AMD engineers ran TigerGraph’s Graph Database benchmark in order to compare the performance of standard N2D VMs to Confidential N2D VMs. The figure below, showing results on a six-node cluster with 16 vCPU instances, demonstrates that on average, there is a performance impact of ~6.73% when using Confidential VMs. This benchmark tests analytic query performance for 3 different types of queries including khop6, WCC and PageRank. The test was done using a Twitter dataset which includes 41.6M vertices and 1.47B edges. For more information, see TigerGraph on Google Compute Engine with N2D Instances.
Monte Carlo and Black-Scholes Simulations
Financial Services Industry (FSI) companies can take advantage of the cost-effectiveness, scalability and high availability of cloud-based services, but have compliance and data security concerns that need to be addressed.
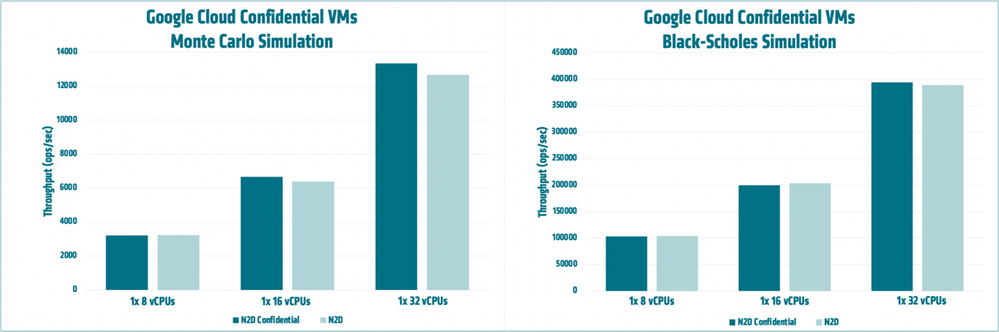
Monte Carlo simulation is a stochastic method extensively used in finance to model option pricing, portfolio management and risk assessment. AMD engineers ran a Monte Carlo simulation benchmark in order to compare the performance of standard N2D VMs to Confidential N2D VMs. The figure below, showing results on 8, 16, and 32 vCPU instances, show comparable performance between the standard and Confidential VMs.
The Black-Scholes Merton formula is a closed-form solution used for computing call and put options. AMD engineers ran a Black-Scholes simulation benchmark in order to compare the performance of standard N2D VMs to Confidential N2D VMs. The figure below, showing results on 8, 16, and 32 vCPU instances, show comparable performance between the standard and Confidential VMs.
Computational Fluid Dynamics (CFD)
OpenFOAM® is an open source CFD tool with a large user base across engineering and science in both the commercial and academic sectors. OpenFOAM can solve a wide range of complex fluid flows involving chemical reactions, turbulence, and heat transfer, as well as acoustics, solid mechanics and electromagnetics.
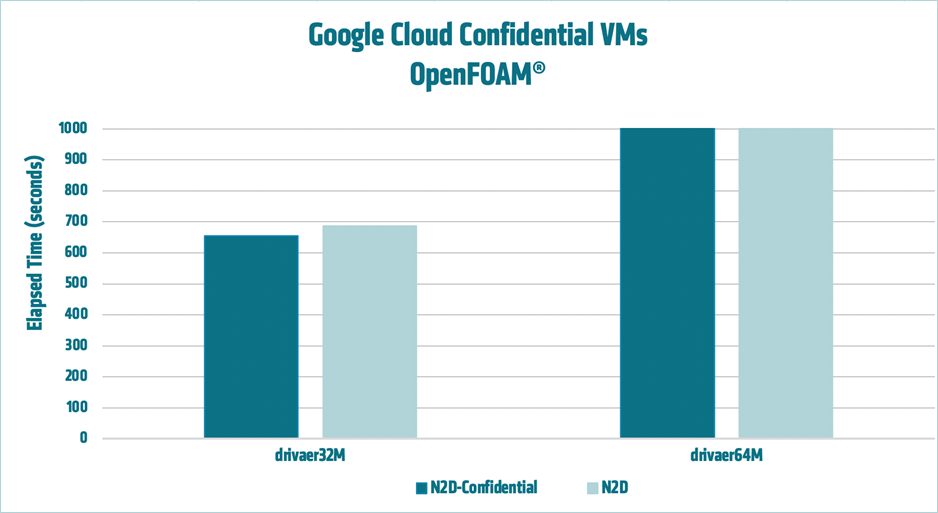
AMD engineers ran OpenFOAM benchmark tests in order to compare the performance of standard N2D VMs to Confidential N2D VMs. The figure below, showing results using the standard drivaer32M and drivaer64M models on a single instance with 224 vCPUs, shows comparable performance between the standard and Confidential VMs.
In summary, Google Confidential VMs powered by AMD’s record setting AMD EPYC processors using Secure Encrypted Virtualization can offer cloud customers peace of mind while delivering the performance, scalability, and reliability they’ve come to expect from Google Compute Engine. Google Confidential Computing VMs can help transform the way your organization processes data in the cloud while helping to preserve confidentiality and privacy, particularly useful in regulated industries such as Financial Services and Healthcare.
For more cloud solutions using AMD EPYC powered Google Cloud N2D and Confidential VMs, visit the AMD EPYC Tech Docs and White Papers Library.
End Notes
For more information related to security compliance in the Financial Services industry, see:
https://cloud.google.com/files/financial-services-compliance-overview.pdf*
https://www.fsistrategies.com/modern-workplace/about-security-and-compliance/*
Raghu Nambiar is a Corporate Vice President for AMD. His postings are his own opinions and may not represent AMD’s positions, strategies or opinions. Links to third party sites are provided for convenience and unless explicitly stated, AMD is not responsible for the contents of such linked sites and no endorsement is implied.
*Links to third party sites including social media feeds are provided for convenience and unless explicitly stated, AMD is not responsible for the contents of such linked sites and no endorsement is implied.
DISCLAIMER
The information contained herein is for informational purposes only and is subject to change without notice. While every precaution has been taken in the preparation of this document, it may contain technical inaccuracies, omissions and typographical errors, and AMD is under no obligation to update or otherwise correct this information. Advanced Micro Devices, Inc. makes no representations or warranties with respect to the accuracy or completeness of the contents of this document, and assumes no liability of any kind, including the implied warranties of noninfringement, merchantability or fitness for particular purposes, with respect to the operation or use of AMD hardware, software or other products described herein. No license, including implied or arising by estoppel, to any intellectual property rights is granted by this document. Terms and limitations applicable to the purchase or use of AMD’s products are as set forth in a signed agreement between the parties or in AMD’s Standard Terms and Conditions of Sale.
©2020 Advanced Micro Devices, Inc. All rights reserved. AMD, the AMD Arrow logo, EPYC, and combinations thereof are trademarks of Advanced Micro Devices, Inc. Google and Google Cloud Platform are trademarks or registered trademarks of Google, Inc. in the United States and other countries. MySQL is a trademark of Oracle Corporation in the United States and other counties. Apache is a trademark of The Apache Software Foundation. TigerGraph is a trademark of TigerGraph in the US and other countries. Other product names used in this publication are for identification purposes only and may be trademarks of their respective companies.