- AMD Community
- Support Forums
- General Discussions
- Researches discover 8 more Spectre class vulnerabi...
General Discussions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Researches discover 8 more Spectre class vulnerabilities in ARM, Intel processors. Effect on AMD unknown.
https://www.tomshardware.com/news/spectre-ng-vulnerabilities-intel-arm-amd,37002.html
The online German computer magazine Heise.de is reporting that eight new Spectre-class vulnerabilities have been discovered. The vulnerabilities purportedly affect Intel and ARM processors, but the impact on AMD processors remain unknown.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anybody heard of any proven cases of Spectre or Meltdown being used to compromise a system? There's lot's of "could be used" or "might be used" but I can't find anything stating it "was used".
I think these two vulnerabilities should have been kept under wraps. But I guess that's the internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are no known Spectre or Meltdown exploits outside the lab, though going by what was revealed they are much more difficult to exploit than, say, finding a flaw in the OS or software, much like how you can freeze RAM chips to steal information, and it's really not that severe considering these vulnerabilities existed for years without discovery.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At least it says they wont release the vulnerabilities until it's patched this time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The original Spectre and Meltdown weren't due to be released until patches were, but someone leaked it to the media.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not patching my i7 3930K\ Win 7 Pro because of the possibility of a performance hit (Intel) or not being able to boot (AMD). There doesn't seem to be any real threat to me. If I owned a corporation I would. But I don't.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Easier for you, since Spectre updates are meant to work in conjunction with additional updates in the BIOS, you're on a dead platform so you never have to touch it, whereas us on long term Socket AM4 or new Intel platforms do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it's the mainboard manufacturer that writes the patch code into the bios update?
Edit
Did some checking into it. Yea, it's a bios update. But it looks like a zoo with Microsoft, Intel and the mainboard manufacturers. Nothing I want to get involved with. I'm hitting 80FPS avg. on Ultra @ 1440p in Far Cry 5. No need to upgrade into that mess.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The performance impact of the patches outside of professional and server applications is minimal, games benchmark within the margin of error from both companies. Storage takes the biggest hit, which if you run a server farm with hundreds or thousands of disks cranking away running cloud based VMs and the like is bad news, but home users aren't affected. The biggest problem comes in with rushed patches causing bootloops and other garbage from Microsoft.
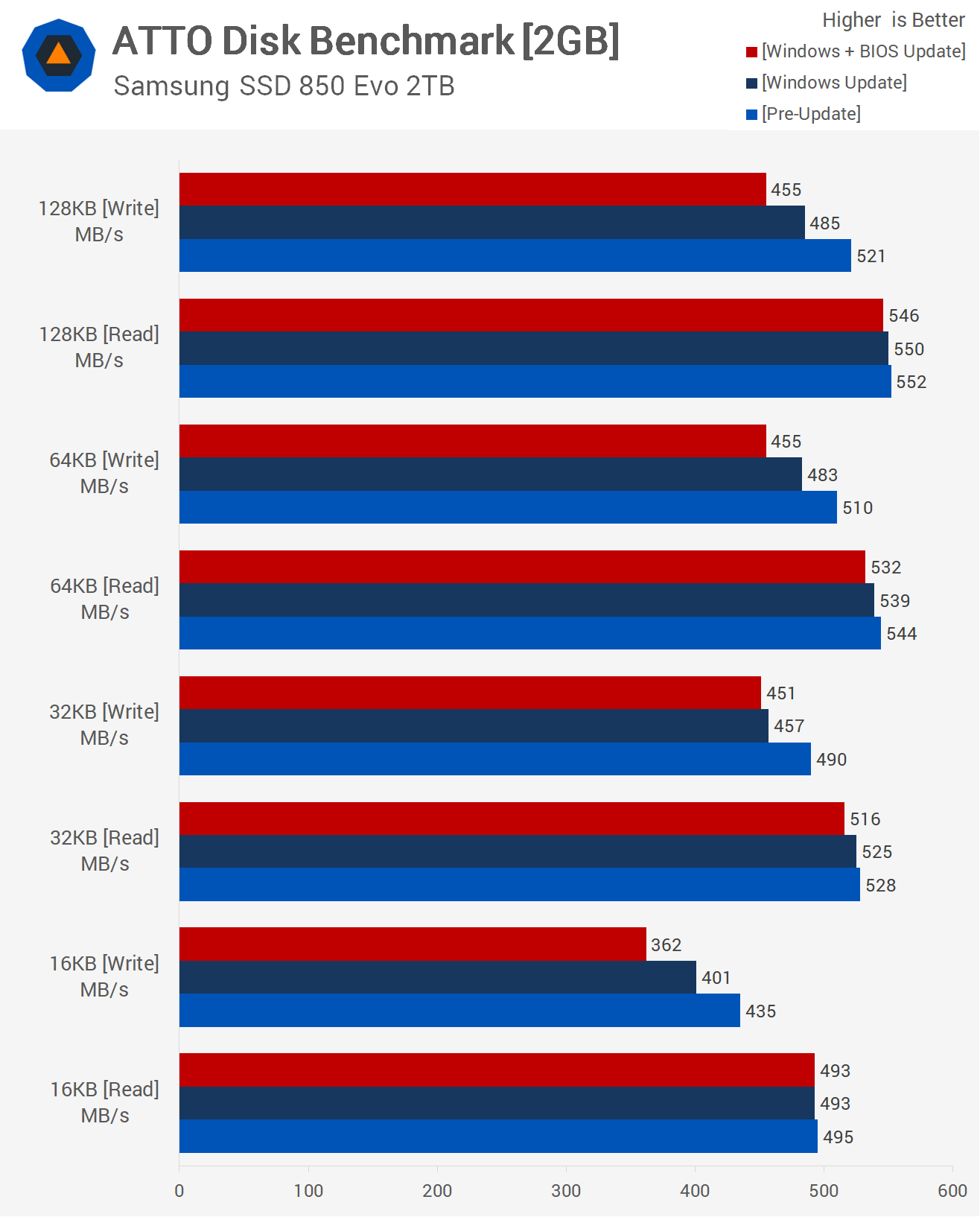
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Proposed solution to spectre class:
If there is some abuse detected by the CPU (eg attempted out of bounds read) can't a new gen of CPUs flip a flag and store Program Counter (and whatever other useful info) so that the OS can be made aware and take appropriate action to deprivilege the thread (eg. make it run in safe mode, with no L1 and L2 cache access, and no future speculative execution).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AMD and Intel both have Spectre fixes included in their next generation chips. What those fixes are exactly they aren't saying, but it's going to make the OS patches obsolete.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The trick is how does the OS differentiate between what does and does not need patching. My guess is as long as the software patches are in Windows at all it will still affect chips that don't need the patch too. The only way you move forward from that is to no longer support the older chips. I can see that coming eventually but not likely for several years. If they cut off chips that people bought since last year until next year or later when the new tech comes out, people would riot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A new patch that removes the old patches if a CPU with the fixes is detected is what it would take, shouldn't be too difficult for Microsoft, they've had a lot of experience with that sort of thing since moving to the idiotic bundled patch form.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So guessing then that it either applies or does not apply the software fix based on the hardware ID of the processor?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, does or does not even install the patch, ideally that's going to be the way it goes, but knowing Microsoft they'll screw it up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So technically then, they will need to remove the current patch on everything when the time comes then apply a new patch for the processor that are still vulnerable in hardware. Yah, I most certainly see that getting messed up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They at least have a year to get ready for it, the fixes aren't going to be ready until Ryzen 2 and whatever succeeds Coffee Lake.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have posted several articles on the faults on my site, read it and see why I get 500 organic referrals a day
